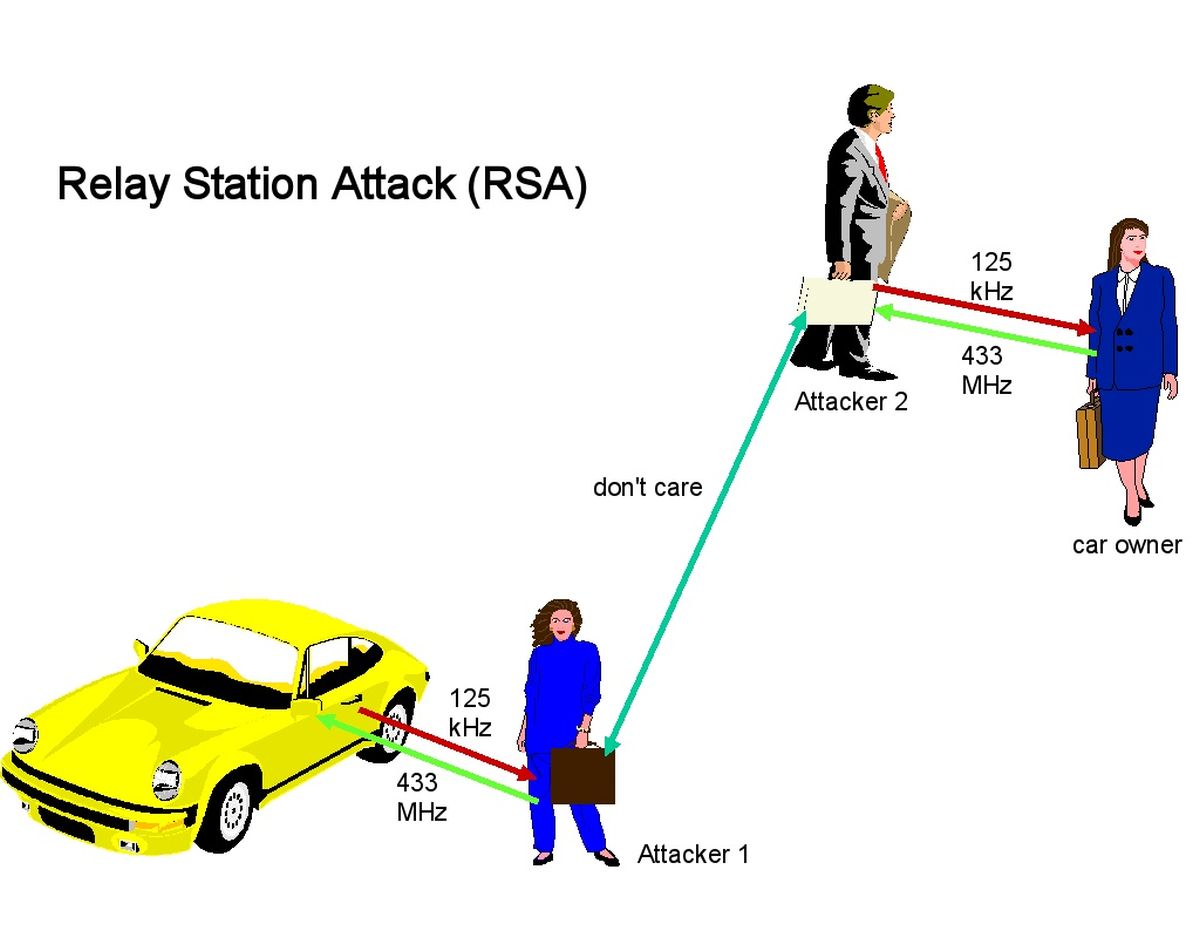
To prove how easy it is for a hacker to break into a Tesla EV, a researcher by the name of Sultan Qasim Khan, from the security firm, NCC Group, recently devised a hack that enables him the ability to unlock millions of Teslas – along with several other Bluetooth capable devices – even when the keycard or the phone it is linked to is hundreds of kilometres away. The kicker here, Khan says, is that the process simply requires some creative coding and approximately US$100 (~RM440) worth of hardware. The method is known as a relay attack and in the simplest of descriptions, the process requires two assailants to be in play. As per Ars Technica’s explanation, the first attacker (Attacker 1) will need to be in close proximity to the Tesla, while the second threat actor (Attacker 2), will be required to stay in close proximity of the car’s owner and phone. In order to unlock the vehicle. Both the first and second attacker must have an open internet connection, obviously, in order for the data to transfer between them. Once the stage is set, Attacker 1 will then proceed to use their own Bluetooth-enabled device to send the Tesla a signal, all the while impersonating the real owner’s phone. This will then prompt the Tesla to reply with an authentication request, at which point, Attacker 1 sends the request to Attacker 2, who in turn proceeds to send said request to the authenticating phone. From there, the owner’s phones responds with the appropriate credentials, which are then relayed back to Attacker 1 via Attacker 2. Again, this is just one of multiple examples that hackers can gain access to a Tesla, but scarier still: this is a feature of Low-Energy Bluetooth (BLE), and not a bug. Sometimes, hackers may not even be required to work in teams, in order for a relay attack to take off. Sometimes, all it takes is prep work in advance; once a hacker has determined the location of a Tesla or when the car is likely going to be, they could then go about planting relaying devices in and around the car. Then, when the car moves into Bluetooth range, the whole process explained above can be repeated, sans a second human attacker. A solution to this issue, NCC Group says, is that Tesla owners disable the vehicle’s passive entry function altogether. Another solution, they said, is to add a PIN to the authentication process, for an extra layer of security, as well as placing time limits on the entry system, if the phone or key has been idle for more than a minute. (Source: Ars Technica, Jalopnik)